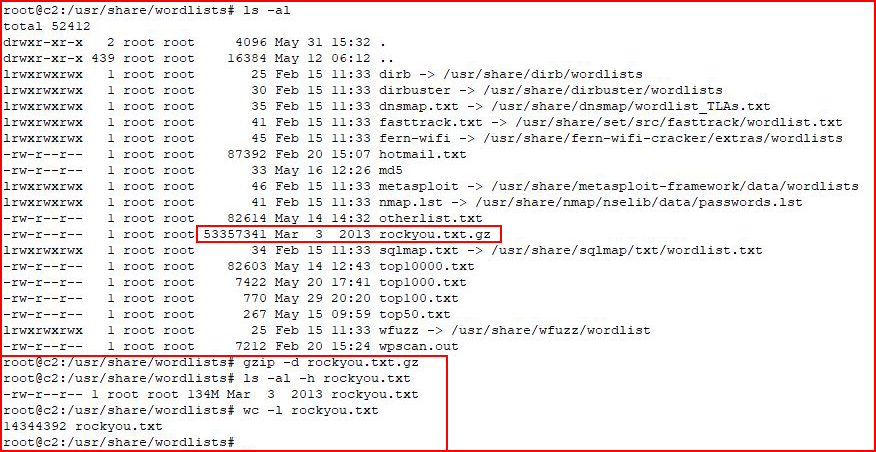
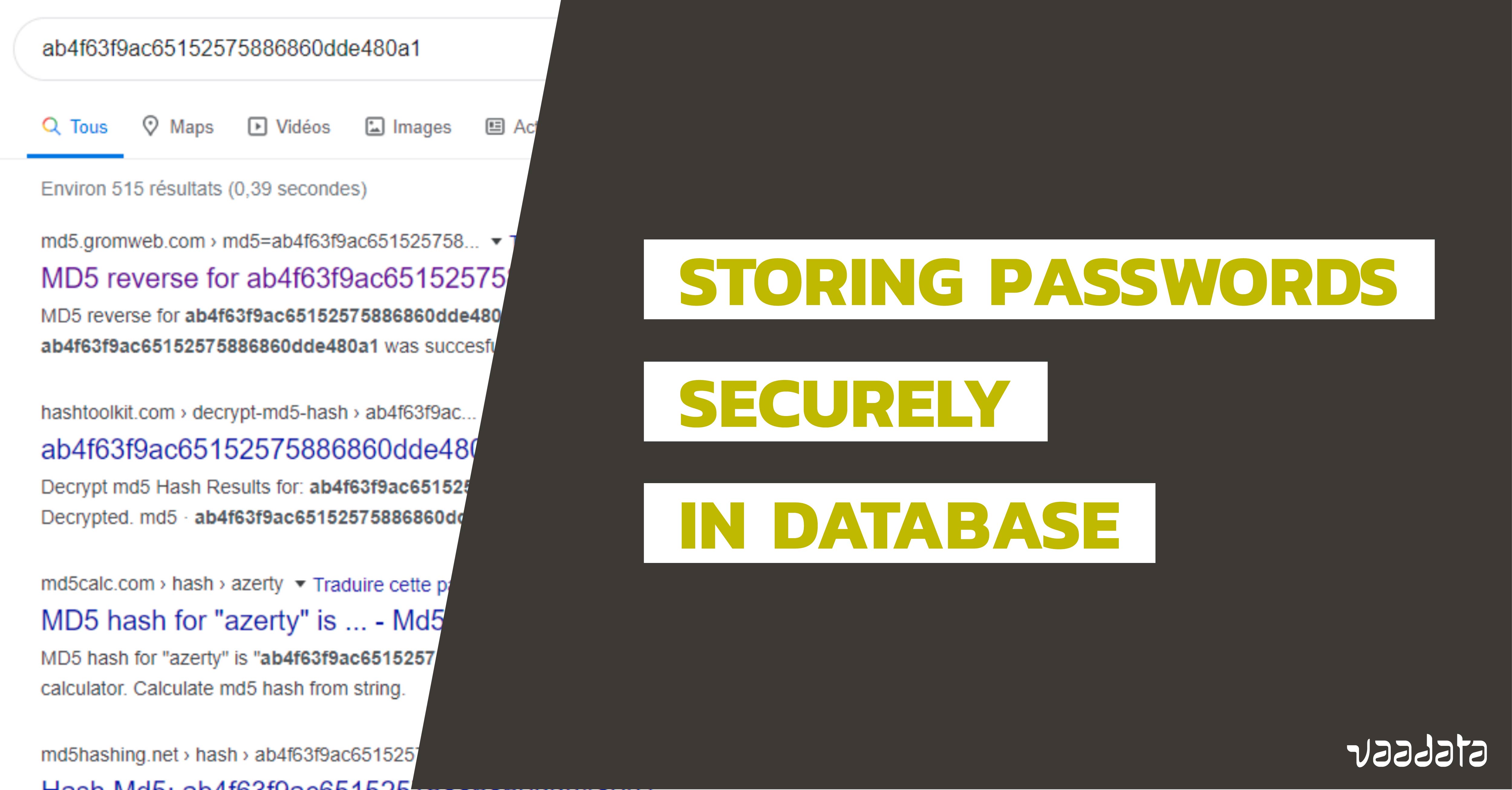
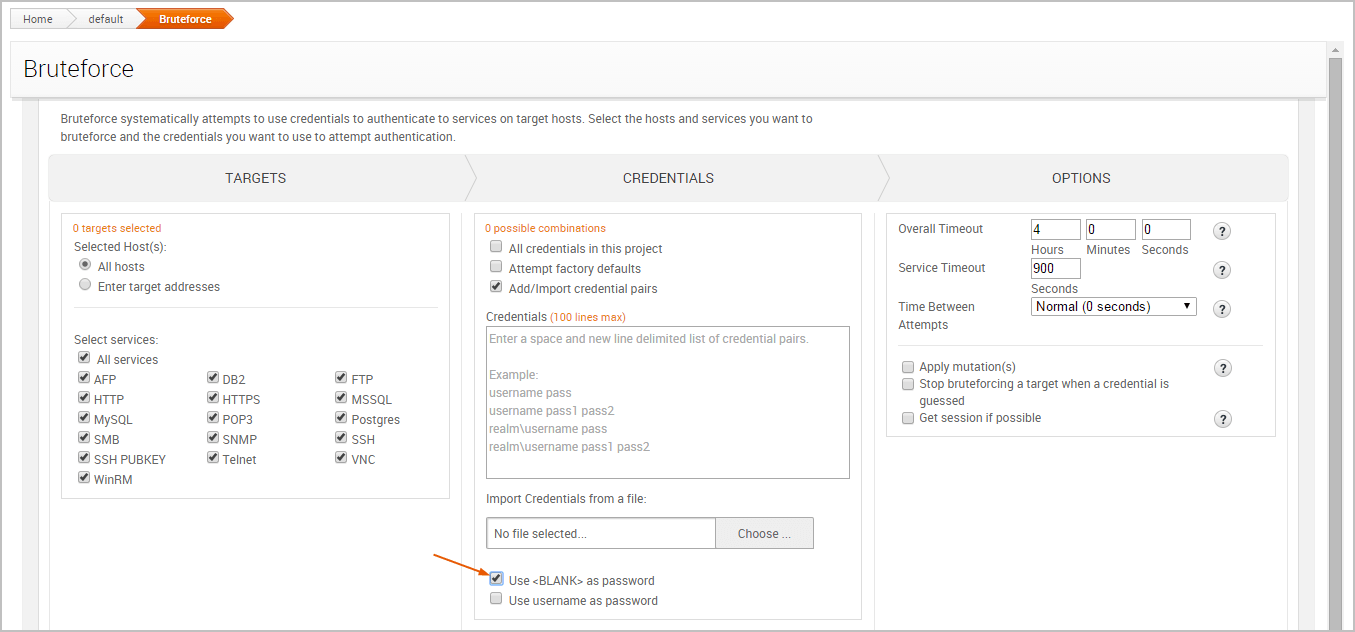
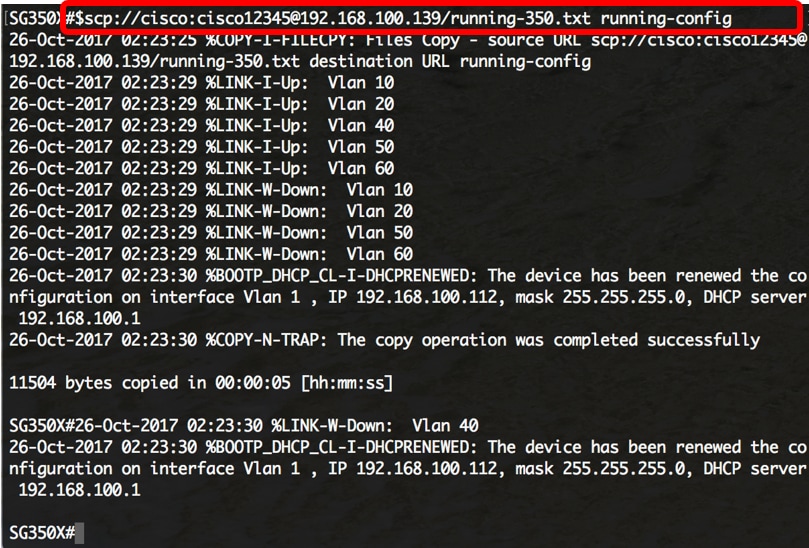
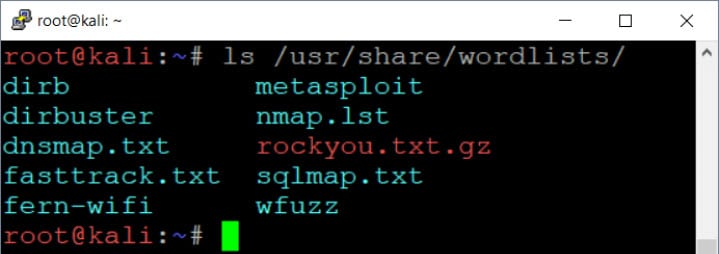
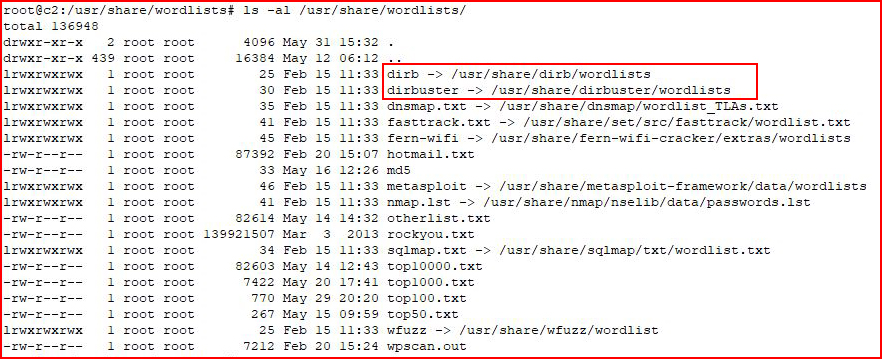
GitHub - ihebski/Pentest-chainsaw: Scrapes Router Passwords From http://www.routerpasswords.com ,more then +300 product

Tracking Diicot: an emerging Romanian threat actor - Cado Security | Cloud Forensics & Incident Response
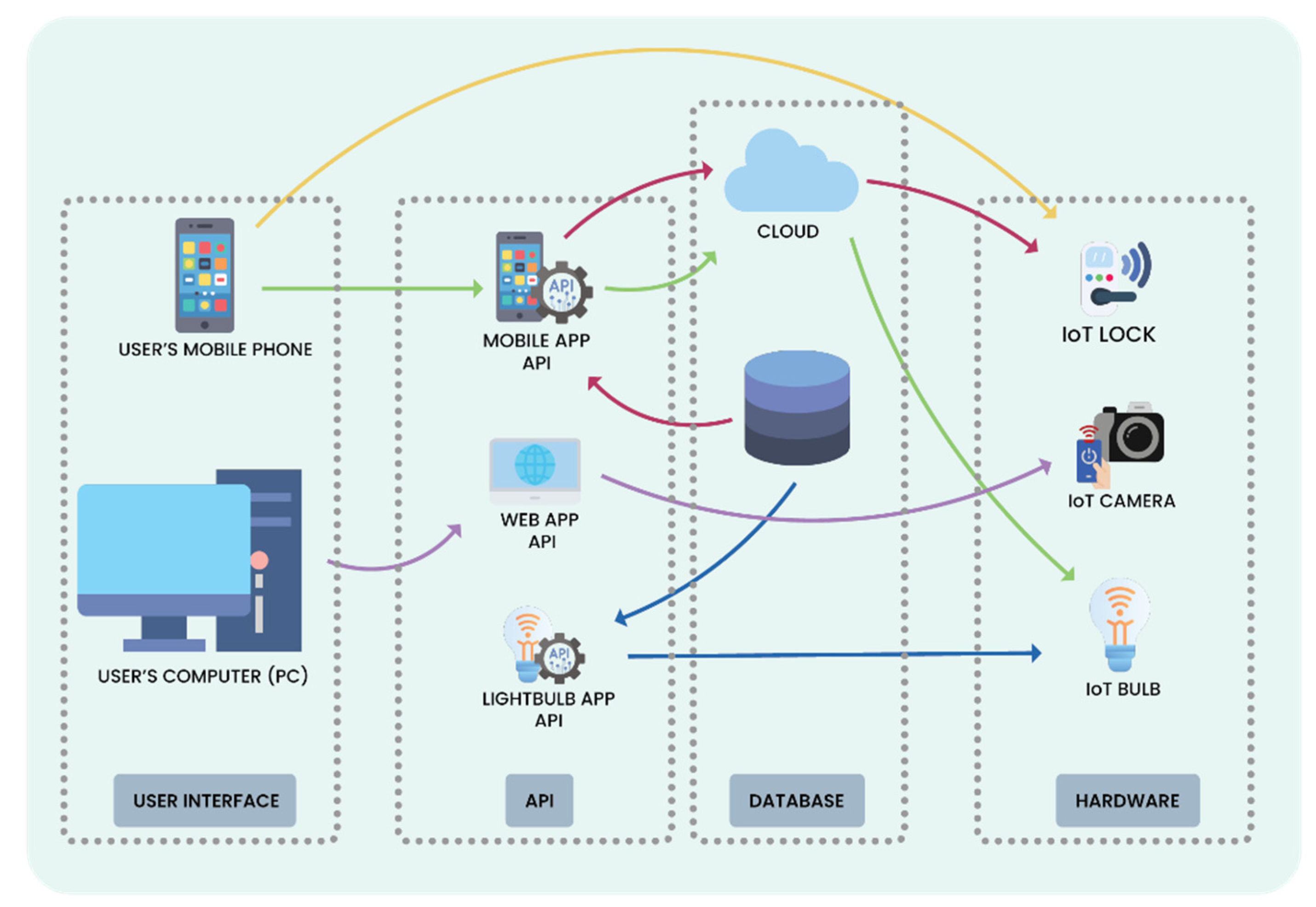
Future Internet | Free Full-Text | Automated Penetration Testing Framework for Smart-Home-Based IoT Devices